National Security Agency
(Intelligence agency) | |
|---|---|
 Fort Meade, Maryland USA | |
 | |
| Motto | "Defending Our Nation. Securing The Future." |
| Predecessor | Armed Forces Security Agency |
| Formation | November 4, 1952 |
| Parent organization | US/Department/Defense |
| Headquarters | Fort Meade, Maryland |
| Leader | Director of the National Security Agency |
| Subgroups | National Tactical Integration Office |
| Staff | ? |
| Interest of | 'BillCaseyHoneyPot', James Bamford, Fred Chang, Ty Clevenger, Scott Shane, Elizabeth Vos |
| Member of | United States Intelligence Community |
| Founder of | Main Core |
| Exposed by | James Bamford |
| "No Such Agency". Spook agency working closely with Silicon Valley | |
The National Security Agency is a notoriously secretive US intelligence agency, nominally responsible for signals intelligence and information assurance. It became infamous in 2013 after the commercially-controlled media gave prominence to Edward Snowden's revelations about its mass data collection programs.[1] The Washington Post reported in 2018 that it has suffered from poor morale and lost many of its most capable employees since 2015.[2]
Contents
- 1 Official Narrative
- 2 Problems
- 3 Activities
- 4 Exposure
- 5 Relationship with other intelligence agencies
- 6 Events carried out
- 7 A National Security Agency victim on Wikispooks
- 8 Related Quotations
- 9 Employee on Wikispooks
- 10 Related Documents
- 11 A document sourced from National Security Agency
- 12 References
Official Narrative
The NSA promises on its website to "protect national security interests by adhering to the highest standards of behavior".[3]
“Your Data: If You Have Nothing to Hide, You Have Nothing to Fear”
NSA [4]
Problems
The NSA is so shrouded in secrecy that there is no way to know what it is doing, never mind to check its claim to "adhere to the highest standards of behavior". For example, in 1964 the US Congress passed by a great majority a bill giving the Director of the NSA the power to fire at will any employee without due cause - leading the Washington Post to write: "This is the very definition of arbitrariness. It means that an employee could be discharged and disgraced on the basis of anonymous allegations without the slightest opportunity to defend himself."[5]
The NSA appears to be completely controlled by he US deep state. Rather than defending US citizens' data by publicising flaws found in computer code, for example, it has long been using zero day exploits for its own purposes and in 2014 was specifically authorised to do to by Barack Obama.[6] The NSA has denied that it was aware of the Heartbleed bug, but other sources report that the agency used it regularly for years, and decided not to warn anyone else that their data was at risk.[7]
Whistleblowers
The agency had several whistleblowers throughout the years, most where harassed for dissent or going public:
- Kirk Wiebe
- William Binney
- Mark Klein (working for AT&T)
- Thomas Drake
- Russ Tice
- Edward Snowden
Activities
John Perkins wrote in Confessions Of An Economic Hitman that he was recruited by Einar Greve, NSA liaison. His book was so popular that in 2006 it prompted an official denial by the US State Department, which claimed that Perkins' claim was not credible because "the National Security Agency is a cryptological (codemaking and codebreaking) organization, not an economic organization." Little was known publicly about the NSA's activities at the time of this counterclaim, but subsequently, leaks and whistleblowers have shed more light on them.[8]
"Cyberterrorism"
- Full article: “Cyberterrorism”
- Full article: “Cyberterrorism”

The NSA is probably the most advanced and active group worldwide in the area of cyberterrorism. Bruce Schneier observes that "The National Security Agency is lying to us. We know that because data stolen from an NSA server was dumped on the Internet. The agency is hoarding information about security vulnerabilities in the products you use, because it wants to use it to hack others' computers."[9]
Stuxnet
- Full article: Stuxnet
- Full article: Stuxnet
Stuxnet was the first piece of malware proven to be an NSA production. The 2016 film Zero Days quotes an anonymous source that this was developed in concert with Unit 8200 and that if it had not been modified by Unit 8200 and released into Iran in this form, it might have never been detected.[10]
Other malware
The NSA created malware, some of which was published by the group Equation Brokers and was compromising security of a lot of Microsoft Windows users.[11]
"Cyberespionage"
- Full article:
 Cyberespionage
Cyberespionage
- Full article:
The NSA (or perhaps Unit 8200)[12] is reckoned to be the world's leading developer of cyberespionage tools, a realisation which has gained traction particularly since the Edward Snowden Affair. Documents released by Snowden have pointed the NSA's close collaboration with GCHQ.
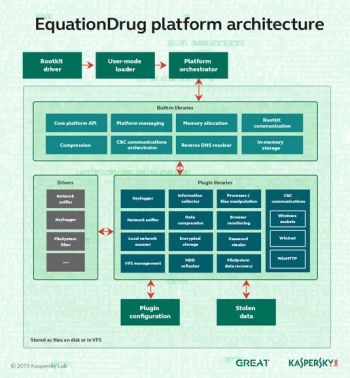
In 2015 multiple revelations gave insight on the NSA's cyberterrorism capabilities. In March 2015, Kaspersky Lab revealed details of the EquationDrug cyberespionage platform, which resembles a "mini operating system" due to the use of kernel-mode and user-mode components which interact with each other via a custom message-passing interface. Over 100 plugins are suspected and the existence of Windows 9X modules suggests that it may well date back to the 1990s. Its connection to the NSA is currently somewhat tenuous - resting on text strings, timezone and filestamp data, though considering the platform's sophistication, no alternative teams of developers have been suggested.
Mass Surveillance
- Full article: Universal Surveillance
- Full article: Universal Surveillance
During the cold war, the NSA watch list included anti-war activists and civil rights leaders such as Martin Luther King and Whitney Young, as well as Senator Frank Church.[13] “The National Security Agency has for years controversially collected the call records of Americans from cell providers like AT&T and Verizon (which owns TechCrunch), despite the questionable legality.” [14]
Technological
The NSA's mass surveillance is facilitated by decades of work for using a variety of techniques to insert backdoors and other weaknesses into security products and protocols.
“I worked with the National Security Agency on the design of a secured version of the internet but we used classified security technology at the time and I couldn't share that with my colleagues. If I could start over again I would have introduced a lot more strong authentication and cryptography into the system.”
Vint Cerf (7 Apr 2014) Vint Cerf wanted to make internet secure from the start, but secrecy prevented it [15]
In 2004, a division of the NSA called the National Tactical Integration Office fitted a 62-foot diameter airship called the Hover Hammer with an eavesdropping device.[16]
Death of UN-SG Dag Hammarskjöld
- Full article: Dag Hammarskjöld/Premature death
- Full article: Dag Hammarskjöld/Premature death
Susan Williams' book Who Killed Hammarskjöld? points to the existence of NSA radio intercepts of warplanes in the area in which UN Secretary-General Dag Hammarskjöld's plane crashed in Africa which are still top secret after over 50 years. She suggests that this may be due to involvement in a shootdown by Jan van Risseghem.
Exposure
In 1971, Perry Fellwock, the first NSA whistleblower, stated that "there's a lot of corruption too. Quite a few people in NSA are into illegal activities of one kind or another. It's taken to be one of the fringe benefits of the job. You know, enhancing your pocketbook. Practically everybody is into some kind of smuggling".[17]
Cancelled investigation by US DOJ
The US DOJ spent a over year looking at the possibility of indicting the NSA after it was revealed that Richard Nixon had instructed the agency to spy on anti-war protestors. They concluded that such a prosecution would result in too many secrets being revealed in court, and so they created FISA in an effort to prevent future US presidents from using the NSA for domestic political purposes. James Bamford states that this was ineffective because of the ease of subversion of the FISA process.[18]
Edward Snowden Affair
- Full article: Edward Snowden Affair
- Full article: Edward Snowden Affair
Former NSA contractor Edward Snowden collected a series of documents which revealed wholesale, illegal, data collection by the NSA. Shunning anonymity, stating that he had done nothing wrong, but was acting in the interests of the US people and the NSA, Snowden began to release a long series of tranches of the documents through the commercially-controlled media.
The NSA claimed on 2014-01-10 that they could not legally inform congress whether they were collecting data on them, since to do so would violate the law.[19] In February 2014, after legal challenges to their data collection program, the NSA suggested that it might be legally obligated to expand the data collection program to avoid potential charges of destroying evidence.[20]
Mass Surveillance
- Full article:
 Mass surveillance
Mass surveillance
- Full article:
Following James Clapper's flat out lie to the US Congress about data collection, key NSA personnel have repeatedly lied about its mass surveillance programmes, first by denying their existence and later by making wildly exaggerated claims about the effectiveness of such data collection in preventing "terrorism".
In 2014, it was revealed that the NSA collects nearly all the telephone calls made in the Bahamas and Afghanistan.[21]
Brian Patrick O'Callaghan
On Feb 16, 2014, a 36 year old, Brian Patrick O'Callaghan, chief of the NSA's Korea division - whose attorney also said he was involved in the high profile rescue of US Army POW Jessica Lynch - was charged with first degree murder and child abuse.[22]
Relationship with other intelligence agencies
GCHQ
The NSA has long had particularly close links with its British counterpart, GCHQ. In the early 1980s it was suggested that "the relationship between NSA and GCHQ is stronger than any between the NSA and any other American intelligence agency."[23] This relationship does not prevent the NSA spying on the UK. According to Howard Teicher, the former Middle East director of the US National Security Council, the NSA monitored Britain's Al-Yamamah arms deal with Saudi Arabia from its base at Menwith Hill in Yorkshire.[24]
Japan
Japan allowed NSA to maintain at least three bases on its territory and contributed more than half a billion dollars to help finance the NSA’s facilities and operations. In return, NSA has kitted out Japanese spies with powerful surveillance tools and shared intelligence with them, although continuing to spy on Japanese officials itself.[25]
Events carried out
| Event | Description |
|---|---|
| NSA/PRISM | Mass surveillance project carried out by the NSA |
| Project SHAMROCK | NSA surveillance program |
A National Security Agency victim on Wikispooks
| Title | Description |
|---|---|
| François Baroin | French politician who attended the 2014 Bilderberg |
Related Quotations
| Page | Quote | Author | Date |
|---|---|---|---|
| Australia/1975 coup | “There were a number of points of tension between Whitlam's government and the United States intelligence apparatus. Whitlam had close ties with the United States, in 1964 receiving a "Leader" travel grant from the U.S. Department of State to spend three months studying under U.S. government and military officials.
After coming to power, Whitlam quickly removed the last Australian troops from Vietnam. Whitlam government ministers criticised the US bombing of North Vietnam at the end of 1972. The US complained diplomatically about the criticism. In March 1973, US secretary of State William Rogers told Richard Nixon that "the leftists [within the Labor Party would] try to throw overboard all military alliances and eject our highly classified US defence space installations from Australia". In 1973, Whitlam ordered the Australian security organisation ASIS to close its operation in Chile, where it was working as a proxy for the CIA in opposition to Chile's president Salvador Allende. Whitlam's Attorney-General Lionel Murphy used the Australian Federal Police to conduct a raid on the headquarters of the Australian Security Intelligence Organisation (ASIO) in March 1973. CIA Chief of Counter-Intelligence, James Angleton, later said Murphy had "barged in and tried to destroy the delicate mechanism of internal security". Australian journalist Brian Toohey said that Angleton considered then Australian Prime Minister Gough Whitlam a "serious threat" to the US and was concerned after the 1973 raid on ASIO headquarters. In 1974, Angleton sought to instigate the removal of Whitlam from office by having CIA station chief in Canberra, John Walker, ask the director general of ASIO, Peter Barbour, to make a false declaration that Whitlam had lied about the raid in Parliament. Barbour refused to make the statement. In 1974, Whitlam ordered the head of ASIO, Peter Barbour, to sever all ties with the CIA. Barbour ignored Whitlam's order and contact between Australian and US security agencies was driven underground. Whitlam later established a royal commission into intelligence and security. Jim Cairns became Deputy Prime Minister after the 1974 election. He was viewed by US secretary of state Henry Kissinger and defence secretary James Schlesinger as "a radical with strong anti-American and pro-Chinese sympathies". The US administration was concerned that he would have access to classified United States intelligence. Whitlam instantly dismissed ASIS chief WT Robinson in 1975 after discovering ASIS had assisted the Timorese Democratic Union in an attempted coup against the Portuguese administration in Timor, without informing Whitlam's government. Whitlam threatened to reveal the identities of CIA agents working in Australia. He also threatened not to renew the lease of the US spy base at Pine Gap, which was due to expire on 10 December 1975. The US was also concerned about Whitlam's intentions towards its spy base at Nurrungar.” | Wikipedia | 2022 |
| George Carlin | “Hello. We’re the ones who control your lives. We make the decisions that affect all of you. Isn’t it interesting to know that those who run your lives would have the nerve to tell you about it in this manner? Suffer, you fools. We know everything you do, and we know where you go. What do you think the cameras are for? And the global-positioning satellites? And the Social Security numbers? You belong to us. And it can’t be changed. Sign your petitions, walk your picket lines, bring your lawsuits, cast your votes, and write those stupid letters to whomever you please; you won’t change a thing. Because we control your lives. And we have plans for you. Go back to sleep.” | George Carlin | |
| Cryptome | “Cryptome raises serious questions that nobody else on the left or in the media want to talk about, including how Omidar has created a business from Snowden's cache; what exactly Snowden may have been doing while he was working for the CIA prior to his time at NSA (and what else he may have been doing at NSA itself); and why Snowden and The Intercept continue to proselytize for Tor, the anonymization tool, despite its massive funding from the U.S. government, the Pentagon and the national security state.” | Tim Shorrock | February 2016 |
| Ron Johnson | “We met delegation after delegation of European representatives. Basically the entire conversation was about Edward Snowden, about tapping Angela Merkel's phone. But then Charlie Hebdo happened. I haven't heard a word about Edward Snowden or what the American security services were trying to do. What I'm hearing now is 'Where's America?'” | Ron Johnson | 2017 |
| Nieuwsuur | “The AIVD and MIVD are subordinates of the Americans. The Dutch work for the Americans. They do what we tell them to do. They aren't valued because of their capacity, but just because they give us a free passage, that's what the NSA uses them for. (...) Look what France is doing and even they couldn't stop all those terror attacks” | Edward Snowden Nieuwsuur | |
| Manuel Noriega | “In 1992, Noriega was tried and convicted on eight drug trafficking and conspiracy counts in federal court in Miami. His 40-year sentence was reduced by 10 years after a former CIA station chief and a former U.S. ambassador spoke on his behalf.
By that time, I had already begun investigating the story. I found more than reasonable doubt about his guilt. The government prosecuted the case with the testimony of 26 convicted drug traffickers who received plea bargains that allowed them to get out of prison and, in some cases, keep their drug profits. One of them was Carlos Lehder, a neo-Nazi from Colombia, then the most important trafficker ever captured by the United States. He had never met Noriega—and neither had the other dealers who testified against him. U.S. District Judge William Hoeveler, who tried the case, invited me to his home after Noriega's conviction and sentencing for a series of unusual talks in which he expressed concern about how the trial and verdict would be judged. "I hope, in the end, we'll be able to say that justice was served," he said. He and other U.S. officials took solace in the fact that even if the drug conviction was questionable, Noriega was clearly a murderer. But the sources I interviewed raised serious questions about one charge against him. In 1993, Noriega was convicted in absentia in Panama of conspiracy in the 1985 murder of Hugo Spadafora, a political protégé turned opponent. A key piece of evidence was that the National Security Agency had intercepted a remote telephone communication in which Noriega allegedly ordered the killing: "What do you do with a rabid dog?... You cut off its head." Multiple U.S. sources told me the intercept did not exist. They said the NSA did not have the capability at that time to capture communications between Noriega—who was in France when Spadafora was killed—and his minions in the Panamanian jungle. I determined that the charges had been made up in part by a Panamanian newspaper columnist and author, Guillermo Sánchez Borbón. He admitted to me he could cite no source for reporting the killing of Spadafora in a book, In the Time of the Tyrants, that he co-wrote with an American expatriate, Richard Koster. "It is a political book, not a historical book," Sanchez Borbón said. "It has its inexactitudes."” | Manuel Noriega Peter Eisner | 2017 |
| UFO | “So, are Unacknowledged Special Access Programs out of control in the United States? Good question. The term "Special Access Program", let alone "Unacknowledged Special Access Program", is only very seldom mentioned in the media. For example, these terms have not been mentioned at all in relation to the NSA spy revelations in recent years of William Binney and Edward Snowden, even though one would expect that many of the NSA spy programs as PRISM, Stellar Wind, Boundless Informant and JTRIG fell into this category. The term "Special Access Program" did recently surface with regard to the Hillary Clinton email scandals. As Obama's secretary of state, Clinton, against protocol, maintained a private mailbox full of information on all kinds of Special Access Programs. No details on these programs have been provided.” | Joël van der Reijden |
Employee on Wikispooks
| Employee | Job | End | Description |
|---|---|---|---|
| Alan Standorf | Civil employee | 1991 | Alleged to have leaked documents relating to the PROMIS intelligence software. Found dead in 1991. |
Related Documents
| Title | Type | Publication date | Author(s) | Description |
|---|---|---|---|---|
| Document:Affidavit of William Casey | Wikispooks Page | William Casey | An admission by William Casey, DCI, that he approved smuggling of cocaine into USA, having chosen Mena, Arkansas as a shipment point, with the support of Bill Clinton and Bill Weld. Casey names a range of names, including John Poindexter, Robert McFarlane, Oliver North and William Colby, the CIA, NSA and ASA. | |
| Document:Dag Hammarskjöld - US, UK and South Africa still withholding crucial information | Article | 10 October 2019 | Ludwig De Braeckeleer | “Communications sent from the CX-52 cryptographic machine used by Dag Hammarskjöld appear to have been intercepted by British and United States signals and intelligence agencies as a result of a secret interception and decryption setting that those agencies held that enabled them to intercept surreptitiously.” |
| Document:Electronic Espionage - A Memoir | interview | August 1972 | Perry Fellwock | |
| Document:GCHQ and Me: My Life Unmasking British Eavesdroppers | Article | 3 August 2015 | Duncan Campbell | No one at the May 2015 conference on intelligence, security and privacy argued against greater openness. Thanks to Edward Snowden and those who courageously came before, the need for public accountability and review has become unassailable. |
| Document:Google and the NSA | article | 24 August 2013 | Julian Assange | |
| Document:Huawei Hypocrisy | blog post | 7 May 2019 | Craig Murray | Former Deputy PM Nick Clegg said GCHQ's ability "to hack anything from handsets to whole networks … needs to be much better understood". |
| Document:NSA GCHQ and the Death of Gareth Williams | article | 14 November 2011 | Trowbridge Ford | A speculative article connecting the NSA with the death of Gareth Williams |
| Document:The Shadow Factory | Book | 2008 | James Bamford | The workings and scope of the US Military-Intelligence complex focussing particularly on the NSA. Introduction. |
| Document:The Terrorists Among US- Traitors and Terror 3 | article | 21 June 2019 | George Eliason Michael Jasinski | George Eliason interviews professor Michael Jasinski about the dire effects of outsourcing intelligence gathering and information dissemination. |
| Document:The demise of global communications security | Wikispooks Page | 21 September 2005 | Wayne Madsen | |
| Document:Top Secret GCHQ report leaked by Edward Snowden | Article | 28 March 2025 | Matt Kennard | "We know how the UK and US militaries have used RAF Akrotiri to supply and support the genocide in Gaza. We know nothing about how they have mobilised their spying assets on Cyprus to support the slaughter. This is one for the ICC and ICJ." |
A document sourced from National Security Agency
| Title | Type | Subject(s) | Publication date | Author(s) |
|---|---|---|---|---|
| Document:Bitter Roots - The Bases of Present Conflicts in the Middle East | speech | Middle East US/Israel lobby | 1977 | J. Rives Childs |
References
- ↑ About NSA, Frequently Asked Questions, National Security Agency, accessed 1 September 2009.
- ↑ https://www.washingtonpost.com/world/national-security/the-nsas-top-talent-is-leaving-because-of-low-pay-and-battered-morale/2018/01/02/ff19f0c6-ec04-11e7-9f92-10a2203f6c8d_story.html
- ↑ http://www.nsa.gov/about/values/index.shtml
- ↑ http://archive.today/2013.08.31-092612/http://nsa.gov1.info/data/index.html
- ↑ David Kahn, The Codebreakers, Scribner Press, 1967, chapter 19, pp. 672–733.
- ↑ http://www.theregister.co.uk/2014/04/14/obama_allows_nsa_to_exploit_0days_report/
- ↑ http://www.bloomberg.com/news/2014-04-11/nsa-said-to-have-used-heartbleed-bug-exposing-consumers.html
- ↑ http://www.unwelcomeguests.net/Category:NSA
- ↑ https://www.schneier.com/blog/archives/2016/08/the_nsa_is_hoar.html
- ↑ Zero Days
- ↑ https://www.theregister.co.uk/2017/04/21/windows_hacked_nsa_shadow_brokers/
- ↑ http://www.forbes.com/sites/richardbehar/2016/05/11/inside-israels-secret-startup-machine/#4b851243157d
- ↑ http://leaksource.info/2013/09/28/declassified-documents-reveal-nsa-spied-on-vietnam-war-critics-including-mlk-muhammad-ali-and-senator-frank-church/
- ↑ https://techcrunch.com/2019/06/24/hackers-cell-networks-call-records-theft/ TechCrunch , 24 June 2019
- ↑ http://www.theregister.co.uk/2014/04/07/internet_inception_security_vint_cerf_google_hangout/ The Register
- ↑ https://theintercept.com/2017/04/24/nsa-blimp-spied-in-the-united-states/
- ↑ Document:Electronic Espionage - A Memoir
- ↑ http://www.unwelcomeguests.net/290
- ↑ http://www.huffingtonpost.com/2014/01/14/bernie-sanders-nsa-letter_n_4597978.html
- ↑ http://thehill.com/blogs/hillicon-valley/technology/198771-nsa-considers-retaining-phone-data-for-lawsuits
- ↑ http://rt.com/news/160988-wikileaks-nsa-phone-afghanistan
- ↑ http://www.nbcwashington.com/news/local/Father-Charged-With-Adopted-Sons-Death--245972321.html
- ↑ Jonathan Bloch and Patrcik Fitzgerald, British Intelligence and Covert Action, Brandon, 1983, p.64.
- ↑ Michael Smith, The Spying Game, Politico's, 2003, p.429.
- ↑ https://theintercept.com/2017/04/24/japans-secret-deals-with-the-nsa-that-expand-global-surveillance/