Difference between revisions of "Internet/Surveillance"
m (Text replacement - "|wikipedia=http://en.wikipedia.org" to "|wikipedia=https://en.wikipedia.org") |
m (tidy references) |
||
| (12 intermediate revisions by 2 users not shown) | |||
| Line 2: | Line 2: | ||
|wikipedia=https://en.wikipedia.org/wiki/Computer_and_network_surveillance | |wikipedia=https://en.wikipedia.org/wiki/Computer_and_network_surveillance | ||
|constitutes=Mass surveillance | |constitutes=Mass surveillance | ||
| − | |image= | + | |image=NSA-Sauron.png |
| − | |description=Wholesale surveillance of the citizenry is the new normal, introduced under the smokescreen of the "war on terror". | + | |image_width=380px |
| + | |description=Wholesale surveillance of the citizenry is the [[new normal]], introduced under the smokescreen of the "[[war on terror]]". | ||
}} | }} | ||
| + | The '''Internet is monitored as never before'''... | ||
==Official narrative== | ==Official narrative== | ||
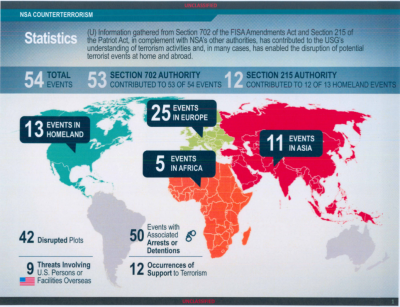
| − | The {{on}} is that mass surveillance of the internet is needed as part of the "[[war on terror]]" to prevent the nebulous threat of [[cyberterrorism]]. | + | [[image:The_54_NSA_events.png|400px|right|thumb|Locations of the 54 "thwarted" terror events. This is a ''serious'' exaggeration - the actual total would appear to be ''zero''.]] |
| + | The {{on}} is that mass surveillance of the internet is needed as part of the "[[war on terror]]" to prevent the nebulous threat of [[cyberterrorism]]. [[NSA]] director [[Keith Alexander]] has repeatedly lied about the illegal mass surveillance programmes, including the spurious but often repeated claim that mass surveillance "thwarted" 54 terror events. Under questioning about this, he reduced that number to one, which did not itself withstand close scrutiny.<ref>http://leaksource.info/2014/01/08/nsa-four-whistleblowers-memo-to-obama-input-for-your-decisions-on-nsa/</ref> The correct figure would appear to be zero.<ref>http://www.pclob.gov/SiteAssets/Pages/default/PCLOB-Report-on-the-Telephone-Records-Program.pdf</ref><ref>http://en.alalam.ir/news/1525126</ref> | ||
==Technical aspects== | ==Technical aspects== | ||
| Line 14: | Line 17: | ||
Closed source software, such as that provided by [[Apple]] or [[Microsoft]] should be assumed to have no effective ability to prevent surveillance against the [[deep state]], whatever 'privacy settings' are presented and whatever claims are made to the contrary. | Closed source software, such as that provided by [[Apple]] or [[Microsoft]] should be assumed to have no effective ability to prevent surveillance against the [[deep state]], whatever 'privacy settings' are presented and whatever claims are made to the contrary. | ||
| − | Open source software allows users to inspect the source and thus (if they have sufficient technical skill) to understand what the software is doing. | + | [[Open source]] software allows users to inspect the source and thus (if they have sufficient technical skill) to understand what the software is doing. |
Security researchers have uncovered systematic abuse by internet service providers in USA, including injection unique identifiers into users' web traffic to allow easy construction of personal browsing profiles.<ref>https://www.techdirt.com/articles/20150115/07074929705/remember-that-undeletable-super-cookie-verizon-claimed-wouldnt-be-abused-yeah-well-funny-story.shtml</ref> | Security researchers have uncovered systematic abuse by internet service providers in USA, including injection unique identifiers into users' web traffic to allow easy construction of personal browsing profiles.<ref>https://www.techdirt.com/articles/20150115/07074929705/remember-that-undeletable-super-cookie-verizon-claimed-wouldnt-be-abused-yeah-well-funny-story.shtml</ref> | ||
| + | |||
| + | By 2017, hundreds of the most popular [[websites]] were using “session replay scripts” to capture every click and keystroke to allow site operators to access information that users didn't actually submit.<ref>https://motherboard.vice.com/en_us/article/59yexk/princeton-study-session-replay-scripts-tracking-you</ref> | ||
===Hardware Backdoors=== | ===Hardware Backdoors=== | ||
| − | In 2014 it was revealed via [[Edward Snowden]] that the [[NSA]] routinely | + | In 2014 it was revealed via [[Edward Snowden]] that the [[NSA]] routinely [[backdoor]]s networking hardware exported from the USA.<ref>http://www.theguardian.com/books/2014/may/12/glenn-greenwald-nsa-tampers-us-internet-routers-snowden</ref> Further, it stands to reason that some "[https://www.wired.com/story/its-not-a-bug-its-a-feature/ bugs]" in commercially available hardware are deliberate design flaws<ref>https://www.theverge.com/2017/9/12/16294904/bluetooth-hack-exploit-android-linux-blueborne saved at [https://web.archive.org/web/20170912155804/https://www.theverge.com/2017/9/12/16294904/bluetooth-hack-exploit-android-linux-blueborne Archive.org] and [http://archive.is/tRSh8 Archive.is]</ref> or planned features<ref>https://www.synacktiv.com/ressources/TCP32764_backdoor_again.pdf saved at [https://web.archive.org/web/20140420023502/http://www.synacktiv.com/ressources/TCP32764_backdoor_again.pdf Archive.org]</ref> to give state actors speedy access to any system. The peculiar destruction of Laptops from [[The Guardian]] that held part of the [[Edward Snowden affair|Snowden]] archive, which was reported about by [[Privacy International]] in 2014,<ref>http://archive.today/2014.05.22-200639/https://www.privacyinternational.org/blog/what-does-gchq-know-about-our-devices-that-we-dont</ref> showed that [[GCHQ]] targeted specific chips on the mainboard and related components, while it could have chosen to instead/or in addition shred the whole hardware to conceal this very specific action. Intelligence agencies, when they get initial access to a system through a browser,<ref>https://medium.com/@nweaver/how-the-nsa-could-hack-almost-any-browser-1b5ab05ac74e saved at [http://archive.is/RMUps Archive.is]</ref> may choose, depending on the capability and value of a target, to not write the data for their surveillance tools on the hard drive where it could more or less easily be found, but on these very chips whose firmware can likely be rewritten, as it is known to be the case with all USB components.<ref>https://www.wired.com/2014/07/usb-security/ saved at [http://web.archive.org/web/20140731080052/http://www.wired.com/2014/07/usb-security/ Archive.org] saved at [http://archive.is/1jWax Archive.is]</ref> This would make it possible to bypass all security monitoring and measures initiated on the level of the [[operating system]] running on the device. It is not clear if the restitution by GCHQ, the way it was done, was deliberate to communicate this very fact, or by mistake. |
==Legal status== | ==Legal status== | ||
| Line 35: | Line 40: | ||
===US=== | ===US=== | ||
[[image:YesWeScan.jpg|right]] | [[image:YesWeScan.jpg|right]] | ||
| − | In contrast to [[Barack Obama]]'s public claim that he "welcomes" a debate on government surveillance, the US federal government has been secretly advising local police forces ''not'' to disclose details about mass surveillance technology suich as the 'Stingray' with which they are sweeping up cellphone data from entire | + | In contrast to [[Barack Obama]]'s public claim that he "welcomes" a debate on government surveillance, the US federal government has been secretly advising local police forces ''not'' to disclose details about mass surveillance technology suich as the 'Stingray' with which they are sweeping up cellphone data from entire neighbourhoods.<ref>http://bigstory.ap.org/article/us-pushing-local-cops-stay-mum-surveillance</ref> |
====Clapper v. Amnesty International==== | ====Clapper v. Amnesty International==== | ||
{{FA|Clapper v. Amnesty International}} | {{FA|Clapper v. Amnesty International}} | ||
| − | According to [[Jameel Jaffer]], deputy legal director of the [[American Civil Liberties Union|ACLU]], who argued [[Clapper v. Amnesty International]] before the [[US Supreme Court]] which challenged [[Foreign Intelligence Surveillance Act of 1978 Amendments Act of 2008|amendments made in 2008]] to the Foreign Intelligence Surveillance Act essentially allow the [[National Security Agency]] (NSA) "to engage in dragnet surveillance of Americans’ international communications", even those "who might not be suspected at all of having done anything wrong," so that "it’s a very broad surveillance statute", "arguably broader than any surveillance statute that Congress has sanctioned in the past."<ref name="dn27-03-2013"> | + | According to [[Jameel Jaffer]], deputy legal director of the [[American Civil Liberties Union|ACLU]], who argued [[Clapper v. Amnesty International]] before the [[US Supreme Court]] which challenged [[Foreign Intelligence Surveillance Act of 1978 Amendments Act of 2008|amendments made in 2008]] to the Foreign Intelligence Surveillance Act essentially allow the [[National Security Agency]] (NSA) "to engage in dragnet surveillance of Americans’ international communications", even those "who might not be suspected at all of having done anything wrong," so that "it’s a very broad surveillance statute", "arguably broader than any surveillance statute that Congress has sanctioned in the past."<ref name="dn27-03-2013">http://www.democracynow.org/2013/2/27/aclu_blasts_supreme_court_rejection_of </ref> The [[US Supreme Court]], by requiring the plaintiffs to show that they, themselves, have been monitored under the law, has essentially created a barrier to judicial review preventing anyone from ever challenging this kind of statute in court as, indeed, nobody can show that they have been monitored under the law since the government is not disclosing its targets.<ref name="dn27-03-2013"/> |
| + | |||
| + | ===Russia=== | ||
| + | In 1998, the [[Russian]] government passed a law stating that all [[Internet Service Providers]] must install a computer black box with a link back to the [[FSB]] to record all the Internet activity of their users. | ||
| − | |||
| − | |||
| − | |||
{{SMWDocs}} | {{SMWDocs}} | ||
| + | |||
==References== | ==References== | ||
{{reflist}} | {{reflist}} | ||
| − | |||
Latest revision as of 07:01, 9 August 2021
(Mass surveillance) | |
|---|---|
 | |
| Interest of | Yasha Levine |
| Wholesale surveillance of the citizenry is the new normal, introduced under the smokescreen of the "war on terror". | |
The Internet is monitored as never before...
Contents
Official narrative
The official narrative is that mass surveillance of the internet is needed as part of the "war on terror" to prevent the nebulous threat of cyberterrorism. NSA director Keith Alexander has repeatedly lied about the illegal mass surveillance programmes, including the spurious but often repeated claim that mass surveillance "thwarted" 54 terror events. Under questioning about this, he reduced that number to one, which did not itself withstand close scrutiny.[1] The correct figure would appear to be zero.[2][3]
Technical aspects
Large scale surveillance is carried out routinely by a variety of strategies. Individual, personalised, surveillance is carried out against specific targets.
Software
Closed source software, such as that provided by Apple or Microsoft should be assumed to have no effective ability to prevent surveillance against the deep state, whatever 'privacy settings' are presented and whatever claims are made to the contrary.
Open source software allows users to inspect the source and thus (if they have sufficient technical skill) to understand what the software is doing.
Security researchers have uncovered systematic abuse by internet service providers in USA, including injection unique identifiers into users' web traffic to allow easy construction of personal browsing profiles.[4]
By 2017, hundreds of the most popular websites were using “session replay scripts” to capture every click and keystroke to allow site operators to access information that users didn't actually submit.[5]
Hardware Backdoors
In 2014 it was revealed via Edward Snowden that the NSA routinely backdoors networking hardware exported from the USA.[6] Further, it stands to reason that some "bugs" in commercially available hardware are deliberate design flaws[7] or planned features[8] to give state actors speedy access to any system. The peculiar destruction of Laptops from The Guardian that held part of the Snowden archive, which was reported about by Privacy International in 2014,[9] showed that GCHQ targeted specific chips on the mainboard and related components, while it could have chosen to instead/or in addition shred the whole hardware to conceal this very specific action. Intelligence agencies, when they get initial access to a system through a browser,[10] may choose, depending on the capability and value of a target, to not write the data for their surveillance tools on the hard drive where it could more or less easily be found, but on these very chips whose firmware can likely be rewritten, as it is known to be the case with all USB components.[11] This would make it possible to bypass all security monitoring and measures initiated on the level of the operating system running on the device. It is not clear if the restitution by GCHQ, the way it was done, was deliberate to communicate this very fact, or by mistake.
Legal status
The legal status of mass internet surveillance is seldom questioned by the commercially-controlled media. Many national governments have passed legislation to try to prevent anonymous internet access, for example, by mandating a registry of all internet users and obliging ISPs to save connection and IP address data. Even one decade ago many countries still had consumer privacy legislation in force which mandated the exact opposite, but such legislation was overturned and monitoring is quickly becoming the rule rather than the exception.
Australia
In September 2014, Australian laws were being read which allows law enforcement agencies to obtain a warrant to access data from a computer — but which also redefine “a computer” to mean not only “one or more computers” but also “one or more computer networks”. Since the Internet itself is nothing but a large network of computer networks, it seems difficult to avoid the conclusion that the bill may allow the spy agency to carry out surveillance on the entire Internet with a single warrant.[12]
New Zealand
In May 2014, New Zealand passed the Telecommunications (Interception Capability and Security) Act (TICSA), which mandates that ISPs use specified hardware for their networking and would only be allowed to build a network subject to certain specifications. They must get government approval for their building of internet infrastructure and must ensure that government agencies can access customer data and connections when needed.[13]
UK
GCHQ have admitted to collecting millions of images from unwitting computer users' webcams, some of which are pornographic in nature.[14] In response to a lawsuit by a coalition of internet privacy groups, Charles Farr, the Director General of the Office for Security and Counter Terrorism, claimed that the indiscriminate interception of UK residents use of Facebook, Google, Hotmail and Twitter was by UK law because they qualified as "external communications", since the platforms were located in US.[15]
US
In contrast to Barack Obama's public claim that he "welcomes" a debate on government surveillance, the US federal government has been secretly advising local police forces not to disclose details about mass surveillance technology suich as the 'Stingray' with which they are sweeping up cellphone data from entire neighbourhoods.[16]
Clapper v. Amnesty International
- Full article: Clapper v. Amnesty International
- Full article: Clapper v. Amnesty International
According to Jameel Jaffer, deputy legal director of the ACLU, who argued Clapper v. Amnesty International before the US Supreme Court which challenged amendments made in 2008 to the Foreign Intelligence Surveillance Act essentially allow the National Security Agency (NSA) "to engage in dragnet surveillance of Americans’ international communications", even those "who might not be suspected at all of having done anything wrong," so that "it’s a very broad surveillance statute", "arguably broader than any surveillance statute that Congress has sanctioned in the past."[17] The US Supreme Court, by requiring the plaintiffs to show that they, themselves, have been monitored under the law, has essentially created a barrier to judicial review preventing anyone from ever challenging this kind of statute in court as, indeed, nobody can show that they have been monitored under the law since the government is not disclosing its targets.[17]
Russia
In 1998, the Russian government passed a law stating that all Internet Service Providers must install a computer black box with a link back to the FSB to record all the Internet activity of their users.
Related Quotation
| Page | Quote | Author |
|---|---|---|
| National Security Agency | “Your Data: If You Have Nothing to Hide, You Have Nothing to Fear” | National Security Agency |
References
- ↑ http://leaksource.info/2014/01/08/nsa-four-whistleblowers-memo-to-obama-input-for-your-decisions-on-nsa/
- ↑ http://www.pclob.gov/SiteAssets/Pages/default/PCLOB-Report-on-the-Telephone-Records-Program.pdf
- ↑ http://en.alalam.ir/news/1525126
- ↑ https://www.techdirt.com/articles/20150115/07074929705/remember-that-undeletable-super-cookie-verizon-claimed-wouldnt-be-abused-yeah-well-funny-story.shtml
- ↑ https://motherboard.vice.com/en_us/article/59yexk/princeton-study-session-replay-scripts-tracking-you
- ↑ http://www.theguardian.com/books/2014/may/12/glenn-greenwald-nsa-tampers-us-internet-routers-snowden
- ↑ https://www.theverge.com/2017/9/12/16294904/bluetooth-hack-exploit-android-linux-blueborne saved at Archive.org and Archive.is
- ↑ https://www.synacktiv.com/ressources/TCP32764_backdoor_again.pdf saved at Archive.org
- ↑ http://archive.today/2014.05.22-200639/https://www.privacyinternational.org/blog/what-does-gchq-know-about-our-devices-that-we-dont
- ↑ https://medium.com/@nweaver/how-the-nsa-could-hack-almost-any-browser-1b5ab05ac74e saved at Archive.is
- ↑ https://www.wired.com/2014/07/usb-security/ saved at Archive.org saved at Archive.is
- ↑ https://www.eff.org/deeplinks/2014/09/australian-government-scrambles-authorize-mass-surveillance
- ↑ http://www.itnews.com.au/News/385149,tough-nz-comms-interception-network-security-law-kicks-in.aspx
- ↑ http://mashable.com/2014/02/27/gchq-webcam-yahoo-images/
- ↑ https://www.privacyinternational.org/press-releases/uk-intelligence-forced-to-reveal-secret-policy-for-mass-surveillance-of-residents
- ↑ http://bigstory.ap.org/article/us-pushing-local-cops-stay-mum-surveillance
- ↑ Jump up to: a b http://www.democracynow.org/2013/2/27/aclu_blasts_supreme_court_rejection_of