Difference between revisions of "Boris Floricic"
(Cryptophone) |
(tidy const) |
||
| Line 11: | Line 11: | ||
|death_cause=Hanging? | |death_cause=Hanging? | ||
|death_place=Berlin | |death_place=Berlin | ||
| − | |constitutes= | + | |constitutes=Hacker |
|victim_of=Premature death | |victim_of=Premature death | ||
}} | }} | ||
Latest revision as of 18:04, 10 March 2022
(Hacker) | |
|---|---|
 | |
| Born | 8 June 1972 |
| Died | 17 October 1998 (Age 26) Berlin |
Cause of death | Hanging? |
| Nationality | German |
| Alma mater | Technical University of Berlin |
| Victim of | Premature death |
| Interests | Cryptography |
German hacker/phreaker with strong interest in cryptography found dead in a park. Ruled a suicide. | |
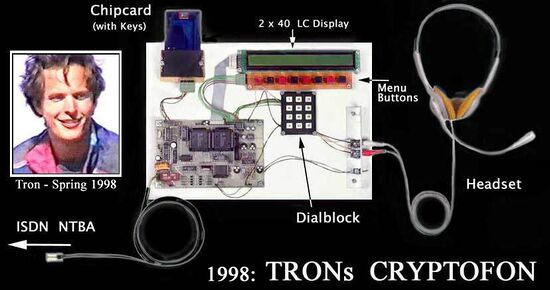
Boris Floricic ('Tron') was a German hacker who invented the first telephone with inbuilt encryption.
Sudden Death
Floricic disappeared on 17 October 1998 and was found dead in a local park in Britz in the Neukölln district of Berlin on 22 October[1] after being hanged from a waistbelt wrapped around his neck. The cause of death was officially recorded as suicide.
Some of his peers in the Chaos Computer Club, as well as his family members and some outside critics, have been vocal in their assertions that Floricic was murdered.[2] It is thinkable that this was a hit by American intelligence, to prevent the license production of the Cryptofon.[3]
Cryptophone
The Cryptophone would have encrypted communication (speech) with inbuilt hardware and would have been much harder to crack than anything that was (or is) available on the consumer market:[4]
A a real-time voice encryption device for the ISDN telephone system. It uses the same algorithms as PGP, namely RSA and IDEA. The whole thing is built as a stream cipher with automatic error correction. The special feature of the Cryptofon is not the used high secure algorithms but their technical realization by discrete components, by digital signal processors (DSPs) which were actually not intended for cryptological applications. Previous systems were based on a 486 or PC architecture. In both the installation of backdoors in the CPU, in the program or in the operating system would be possible.
This was not so easily possible with the completely different system architecture of the Cryptophone. The DSPs were secure because there was never any thought of installing an appropriate backdoor and because they were almost too primitive to install one on the chip. The rest of the cryptophone was hardwired and allowed only special arithmetic operations, but no other program that could run in the background. Everything was controlled not by a PC CPU but by a much simpler microcontroller. These are CPU like, but they are used in PCs only as auxiliary components. For these microcontrollers the same is valid as for the DSPs. And also the program in the EPROMs is too small to hide a backdoor.
External links
- Wiki entry (in German) with a lot of detailed information (Archive)
- Website dedicated to him: tronland.de
References
- ↑ zdnet.co.uk: "High-stakes hacking, Euro-style", by Bob Sullivan, 2000-10-25
- ↑ Hudson, David (28 December 1998). "Out of Chaos Comes Order". Wired.
- ↑ "Important to him was the further development of the Cryptophone to the point of licensed production. For further laboratory work, he could choose between seven locations offered to him. He was leaning towards Berlin, but a final choice had not yet been made." - http://www.tronland.de/
- ↑ http://www.tronland.de/