Difference between revisions of "Institute for Statecraft/Secrecy"
(quote fix) |
m (Robin moved page Integrity Initiative/Secrecy to Institute for Statecraft/Secrecy) |
||
| (16 intermediate revisions by the same user not shown) | |||
| Line 7: | Line 7: | ||
}} | }} | ||
| − | '''The [[Integrity Initiative]] is marked by an intense [[secrecy]]''' | + | '''The [[Integrity Initiative]] is marked by an intense [[secrecy]]''' that suggest it has hidden [[Integrity Initiative/Purposes|purposes]] suggestive of a [[covert operation]] or a [[deep state milieu]] rather than the public [[charity]] that it purports to be. For a multi-million pound operation, it had a low profile until its [[Integrity Initiative/Leak|2018 leak]]. |
==Headquarters== | ==Headquarters== | ||
| − | The [[headquarters]] of the organisation is officially a semi-derilict mill in Fife, [[Scotland]]. A UK MP{{who}} reports after visiting there that none of the locals were aware of the presence of the group. The operational HQ appears to be [[Two Temple Place]], [[London]]. | + | The [[headquarters]] of the organisation is officially a semi-derilict mill in Fife, [[Scotland]], which is due for demolition{{cn}}. A UK MP{{who}} reports after visiting there that none of the locals were aware of the presence of the group. The operational HQ appears to be [[Two Temple Place]], [[London]]. |
| − | ==Integrity Initiative | + | ==Integrity Initiative Handbook== |
| − | + | The [[Integrity Initiative/Leak|leaked]] Integrity Initiative handbook emphasises secrecy. | |
| − | + | {{SMWQ | |
| − | |source_name=Integrity Initiative/Leak | + | |source_name=Integrity Initiative/Leak/1 |
|source_details=iihandbookv2.pdf | |source_details=iihandbookv2.pdf | ||
|source_URL= | |source_URL= | ||
|date=30 May 2018 | |date=30 May 2018 | ||
| − | | | + | |eio=1 |
| − | + | |subjects=Integrity Initiative/Secrecy, Chris Donnelly, Greg Rowett | |
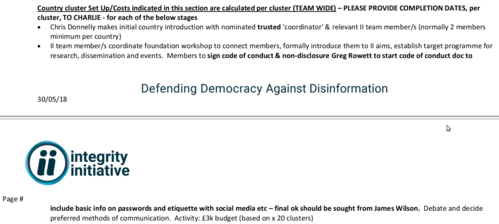
| − | + | |text=* [[Chris Donnelly]] makes initial country introduction with nominated '''trusted''' 'coordinator' & relevant II team member/s (normally 2 members minimum per country) | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |subjects=Integrity Initiative/Secrecy | ||
| − | |text=* Chris Donnelly makes initial country introduction with nominated '''trusted''' 'coordinator' & relevant II team member/s (normally 2 members minimum per country) | ||
* II team member/s coordinate foundation workshop to connect members, formally introduce them to II aims, establish target programme for | * II team member/s coordinate foundation workshop to connect members, formally introduce them to II aims, establish target programme for | ||
| − | research, dissemination and events. Members to '''sign code of conduct & non-disclosure Greg Rowett to start code of conduct doc to include basic info on passwords and etiquette with social media etc – final ok should be sought from [[James Wilson]].''' Debate and decide preferred methods of communication. | + | research, dissemination and events. Members to '''sign code of conduct & non-disclosure [[Greg Rowett]] to start code of conduct doc to include basic info on passwords and etiquette with social media etc – final ok should be sought from [[James Wilson]].''' Debate and decide preferred methods of communication. |
}} | }} | ||
| − | + | The meaning of "etiquette" is further clarified by the perfunctory "Code of Conduct" section: | |
| − | The " | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
{{SMWQ | {{SMWQ | ||
| − | |source_name=Integrity Initiative/Leak | + | |source_name=Integrity Initiative/Leak/1 |
|source_details=iihandbookv2.pdf | |source_details=iihandbookv2.pdf | ||
|source_URL= | |source_URL= | ||
|date=30 May 2018 | |date=30 May 2018 | ||
| − | |subjects= | + | |eio=1 |
| − | |text= | + | |format=QB |
| + | |subjects=Integrity Initiative/Secrecy, Chris Donnelly, Greg Rowett | ||
| + | |text=<u>'''Code of Conduct (Greg to commence with internet etiquette)'''</u><br/> | ||
| + | Anonymity of the team remains paramount. As our activity increases we will, no doubt, attract unwanted attention. | ||
}} | }} | ||
| − | {{SMWQ | + | The leaked Integrity Initiative handbook revealed that they had a £5000 budget for training about [[social media]]: {{SMWQ |
|source_name=Integrity Initiative/Leak | |source_name=Integrity Initiative/Leak | ||
| + | |format= | ||
|source_details=iihandbookv2.pdf | |source_details=iihandbookv2.pdf | ||
|source_URL= | |source_URL= | ||
|date=30 May 2018 | |date=30 May 2018 | ||
| − | |subjects= | + | |subjects=Social media |
| − | |text= | + | |text=Social media training. Activity: £5k '''[[Chris Hernon]] and [[Charlie Hatton]] – [[Jacky Sloane]] to film.''' |
}} | }} | ||
| − | + | It also warns {{SMWQ | |
| − | |source_name=Integrity Initiative/Leak | + | |source_name=Integrity Initiative/Leak/1 |
| + | |source_details=iihandbookv2.pdf | ||
| + | |source_URL= | ||
| + | |format=inline | ||
| + | |image=Integrity Initiative handbook guidance extract.png | ||
| + | |date=30 May 2018 | ||
| + | |eio=1 | ||
| + | |subjects=Integrity Initiative, Plausible deniability, Black ops, Secrecy | ||
| + | |text='''Beware the friendly host who wants to book travel or accommodation on your behalf. Absolutely get their tips on where to stay but avoid getting into tricky scenarios and ensure you follow company guidelines and book everything yourself. If in doubt, ask advice from another team member.''' | ||
| + | }} and reminds readers that {{SMWQ | ||
|format=inline | |format=inline | ||
| + | |source_name=Integrity Initiative/Leak/1 | ||
|source_details=iihandbookv2.pdf | |source_details=iihandbookv2.pdf | ||
|source_URL= | |source_URL= | ||
|date=30 May 2018 | |date=30 May 2018 | ||
| − | |subjects= | + | |subjects=Integrity Initiative/Secrecy, Chatham House rules |
| − | |text= | + | |text=No contact names should be mentioned ([[Chatham House rules]]) reference conversations and spoken word. Contact the report holders for more detailed information on individuals and encounters. |
}} | }} | ||
| − | {{ | + | ==Events== |
| − | | | + | The "Maritime Battle Staff Information Warfare (IW) Study Day" official sensitive bears security classification "Official-Sensitive". One of the key points is {{SMWQ |
| − | | | + | |source_name= |
| − | | | + | |format=inline |
| + | |source_details= | ||
| + | |source_URL= | ||
| + | |text=7. '''Security Classification/[[Chatham House Rule]]'''. The morning session in Fisher Hall will be an academic seminar at official-sensitive. In the afternoon there will be a further plenary session at official-sensitive in the Wells Room led by Mr [[Peter Mattis]] from the [[Jamestown Foundation]] and an invitation only session at a higher classification in the MBS Briefing Room led by Mr [[Olivier Weatherston]] from [[Wilton Park]]. Irrespective of classification, the whole conference will operate under the [[Chatham House rules]]. | ||
| + | |date=22 June 2018}} Use of Chatham House Rules appears to be common (possibly even universal?) for Integrity Initiative private [[meetings]]. | ||
| + | |||
| + | {{SMWQ | ||
| + | |source_name=Integrity Initiative/Leak | ||
| + | |source_details=iihandbookv2.pdf | ||
| + | |source_URL= | ||
| + | |date=30 May 2018 | ||
| + | |subjects=media literacy, Skripal affair | ||
| + | |text=Implementing discernment and media literacy training prog. (using Skripal as a case-study). Activity: £90k '''[[Ben Robinson]], [[Yusuf Desai]], [[Greg Rowett]] ([[Tallinn University]], [[Chester University]]) Teachers Unions?''' | ||
}} | }} | ||
| − | |||
==Instructions on setting up 'clusters'== | ==Instructions on setting up 'clusters'== | ||
| + | {{FA|Integrity Initiative/Clusters}} | ||
The Integrity Initiative hanbook includes the following advice which raises the question of why the need for secrecy before talking about "our programme"? | The Integrity Initiative hanbook includes the following advice which raises the question of why the need for secrecy before talking about "our programme"? | ||
{{SMWQ | {{SMWQ | ||
| Line 81: | Line 94: | ||
|source_details=iihandbookv2.pdf | |source_details=iihandbookv2.pdf | ||
|source_URL= | |source_URL= | ||
| − | |||
| − | |||
|date=30 May 2018 | |date=30 May 2018 | ||
|subjects=Integrity Initiative, Plausible deniability, Black ops, Secrecy | |subjects=Integrity Initiative, Plausible deniability, Black ops, Secrecy | ||
| Line 92: | Line 103: | ||
|source_details=iihandbookv2.pdf | |source_details=iihandbookv2.pdf | ||
|source_URL= | |source_URL= | ||
| − | |||
| − | |||
|date=30 May 2018 | |date=30 May 2018 | ||
|eio=1 | |eio=1 | ||
|subjects=Integrity Initiative, Plausible deniability, Black ops, Secrecy | |subjects=Integrity Initiative, Plausible deniability, Black ops, Secrecy | ||
|text=* [[Chris Donnelly]] makes initial country introduction with nominated '''trusted''' 'cordinator' & relevant II team member/s (normally 2 members minimum per country) | |text=* [[Chris Donnelly]] makes initial country introduction with nominated '''trusted''' 'cordinator' & relevant II team member/s (normally 2 members minimum per country) | ||
| − | * II team member/s coordinate foundation workshop to connect members, formally introduce them to II aims, establish target programme for research, issemmination and events. Members to '''sign code of conduct & non-disclosure [[Greg Rowett] to start code of conduct doc to include basic info on passwords and etiquette with social media etc - final ok should be sought from [[James Wilson]].''' Debate and decide preferred methods of communication. Activity: £3k budget (based on 20 clusters) | + | * II team member/s coordinate foundation workshop to connect members, formally introduce them to II aims, establish target programme for research, issemmination and events. Members to '''sign code of conduct & non-disclosure [[Greg Rowett]] to start code of conduct doc to include basic info on passwords and etiquette with social media etc - final ok should be sought from [[James Wilson]].''' Debate and decide preferred methods of communication. Activity: £3k budget (based on 20 clusters) |
}} | }} | ||
| Line 105: | Line 114: | ||
|source_details=iihandbookv2.pdf | |source_details=iihandbookv2.pdf | ||
|source_URL= | |source_URL= | ||
| − | |||
| − | |||
|date=30 May 2018 | |date=30 May 2018 | ||
|eio=1 | |eio=1 | ||
| Line 118: | Line 125: | ||
|source_details=iihandbookv2.pdf | |source_details=iihandbookv2.pdf | ||
|source_URL= | |source_URL= | ||
| − | |||
| − | |||
|date=30 May 2018 | |date=30 May 2018 | ||
|eio=1 | |eio=1 | ||
| Line 129: | Line 134: | ||
It also points out that the "Professional comprehensive country.. can be anonymous". | It also points out that the "Professional comprehensive country.. can be anonymous". | ||
| − | == | + | ==Contracts== |
| − | The [[ | + | The Integrity Initiative's contract with [[Nico de Pedro]] defines his duties as being "to promote the interests of the Client", but nowhere specifies what these are. Article 2.3 requires that "You must comply with all and any of our work-place policies including those on social media, and information and communications systems." It also contains a confidentiality agreement. Their contract with the University of Macedonia Research Institute of Applied Social and Economic Studies specified that "Neither Party will use, copy, adapt, alter or part with possession of any information of the other which is disclosed or otherwise comes into its possession under or in relation to this Agreement and which is of a confidential nature. "<ref>[[Integrity Initiative/Leak/2]]</ref> |
| − | + | ||
| − | + | =="Open source" research== | |
| − | + | Although it talks about "[[open source]] research", the ''Unleashing the Capacity of Civil Society to [[Counter Disinformation]]'' about the [[EXPOSE network]]. The document's 8 page Appendix on the "Information Sharing Framework" is exclusively focused on "strictly control every stage of the information workflow". The concluding paragraph Clearly, the issuing of centrally managed, encrypted devices is a gold-plated solution which can only be confirmed subject to a better understanding of the future financing lines. Every page has a footer stating: "© PRIVATE AND CONFIDENTIAL DOCUMENT. NOT FOR PUBLIC DISTRIBUTION". | |
| − | + | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | research, | ||
| − | |||
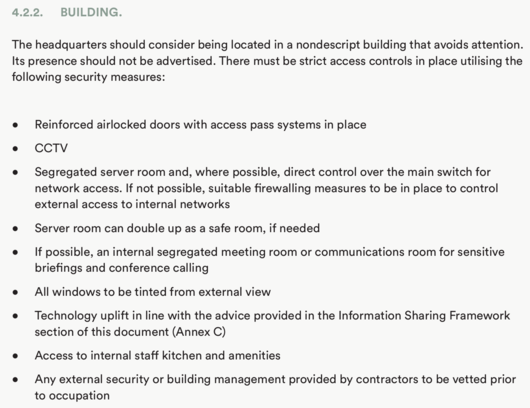
| − | + | [[image:ii_proposed_expose_network_hq.png|left|530px|thumbnail|Security arrangements of the headquarters of the proposed [[EXPOSE Network]]]] | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | | | ||
| − | | | ||
| − | | | ||
| − | | | ||
| − | |||
| − | |||
| − | |||
| − | + | ==Media blackout== | |
| − | + | Detailing the failure to report on the Integrity Initiative, [[21st Century Wire]] asked {{SMWQ | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
|format=inline | |format=inline | ||
| − | | | + | |text=Was there a ‘[[D Notice]]’ issued by the British government forbidding [[mainstream media]] outlets from reporting on the embarrassing [[Integrity Initiative/Leak|leak]] of this clandestine [[propaganda]] operation? |
| − | | | + | |source_name=21st Century Wire |
| − | | | + | |subjects=D Notice, Integrity Initiative/Secrecy, Corporate media/Deep state control, Integrity Initiative/Leak |
| − | |||
| − | |subjects=Integrity Initiative/Secrecy, | ||
| − | |||
}} | }} | ||
| − | |||
| − | |||
| − | |||
| − | |||
{{SMWDocs}} | {{SMWDocs}} | ||
==References== | ==References== | ||
{{reflist}} | {{reflist}} | ||
Latest revision as of 14:27, 8 March 2020
(Secrecy) | |
|---|---|
 | |
| The Integrity Initiative is marked by an intense secrecy and suspicion |
The Integrity Initiative is marked by an intense secrecy that suggest it has hidden purposes suggestive of a covert operation or a deep state milieu rather than the public charity that it purports to be. For a multi-million pound operation, it had a low profile until its 2018 leak.
Contents
Headquarters
The headquarters of the organisation is officially a semi-derilict mill in Fife, Scotland, which is due for demolition[citation needed]. A UK MP[Who?] reports after visiting there that none of the locals were aware of the presence of the group. The operational HQ appears to be Two Temple Place, London.
Integrity Initiative Handbook
The leaked Integrity Initiative handbook emphasises secrecy.
“* Chris Donnelly makes initial country introduction with nominated trusted 'coordinator' & relevant II team member/s (normally 2 members minimum per country)
- II team member/s coordinate foundation workshop to connect members, formally introduce them to II aims, establish target programme for
research, dissemination and events. Members to sign code of conduct & non-disclosure Greg Rowett to start code of conduct doc to include basic info on passwords and etiquette with social media etc – final ok should be sought from James Wilson. Debate and decide preferred methods of communication.”
(30 May 2018) [1]
Emphasis in original
The meaning of "etiquette" is further clarified by the perfunctory "Code of Conduct" section:
“Code of Conduct (Greg to commence with internet etiquette)
Anonymity of the team remains paramount. As our activity increases we will, no doubt, attract unwanted attention.”
(30 May 2018) [1]
Emphasis in original
The leaked Integrity Initiative handbook revealed that they had a £5000 budget for training about social media:
“Social media training. Activity: £5k Chris Hernon and Charlie Hatton – Jacky Sloane to film.”
(30 May 2018) [2]
It also warns “Beware the friendly host who wants to book travel or accommodation on your behalf. Absolutely get their tips on where to stay but avoid getting into tricky scenarios and ensure you follow company guidelines and book everything yourself. If in doubt, ask advice from another team member.” [3] and reminds readers that “No contact names should be mentioned (Chatham House rules) reference conversations and spoken word. Contact the report holders for more detailed information on individuals and encounters.” [3]
Events
The "Maritime Battle Staff Information Warfare (IW) Study Day" official sensitive bears security classification "Official-Sensitive". One of the key points is “7. Security Classification/Chatham House Rule. The morning session in Fisher Hall will be an academic seminar at official-sensitive. In the afternoon there will be a further plenary session at official-sensitive in the Wells Room led by Mr Peter Mattis from the Jamestown Foundation and an invitation only session at a higher classification in the MBS Briefing Room led by Mr Olivier Weatherston from Wilton Park. Irrespective of classification, the whole conference will operate under the Chatham House rules.” [4] Use of Chatham House Rules appears to be common (possibly even universal?) for Integrity Initiative private meetings.
“Implementing discernment and media literacy training prog. (using Skripal as a case-study). Activity: £90k Ben Robinson, Yusuf Desai, Greg Rowett (Tallinn University, Chester University) Teachers Unions?”
(30 May 2018) [2]
Instructions on setting up 'clusters'
- Full article: Integrity Initiative/Clusters
- Full article: Integrity Initiative/Clusters
The Integrity Initiative hanbook includes the following advice which raises the question of why the need for secrecy before talking about "our programme"?
“Be absolutely sure you have good references for people so we know we can trust them before we talk to them about our programme”
(30 May 2018) [2]
The same document continues:
“* Chris Donnelly makes initial country introduction with nominated trusted 'cordinator' & relevant II team member/s (normally 2 members minimum per country)
- II team member/s coordinate foundation workshop to connect members, formally introduce them to II aims, establish target programme for research, issemmination and events. Members to sign code of conduct & non-disclosure Greg Rowett to start code of conduct doc to include basic info on passwords and etiquette with social media etc - final ok should be sought from James Wilson. Debate and decide preferred methods of communication. Activity: £3k budget (based on 20 clusters)”
(30 May 2018) [2]
Emphasis in original
“Code of Conduct (Greg to commence with internet etiquette)
Anonymity of the team remains paramount. As our activity increases we will, no doubt, attract unwanted attention.”
(30 May 2018) [2]
Emphasis in original
“Beware the friendly host who wants to book travel or accommodation on your behalf. Absolutely get their tips on where to stay but avoid getting into tricky scenarios and ensure you follow company guidelines and book everything yourself. If in doubt, ask advice from another team member.”
(30 May 2018) [2]
Emphasis in original
It also points out that the "Professional comprehensive country.. can be anonymous".
Contracts
The Integrity Initiative's contract with Nico de Pedro defines his duties as being "to promote the interests of the Client", but nowhere specifies what these are. Article 2.3 requires that "You must comply with all and any of our work-place policies including those on social media, and information and communications systems." It also contains a confidentiality agreement. Their contract with the University of Macedonia Research Institute of Applied Social and Economic Studies specified that "Neither Party will use, copy, adapt, alter or part with possession of any information of the other which is disclosed or otherwise comes into its possession under or in relation to this Agreement and which is of a confidential nature. "[5]
"Open source" research
Although it talks about "open source research", the Unleashing the Capacity of Civil Society to Counter Disinformation about the EXPOSE network. The document's 8 page Appendix on the "Information Sharing Framework" is exclusively focused on "strictly control every stage of the information workflow". The concluding paragraph Clearly, the issuing of centrally managed, encrypted devices is a gold-plated solution which can only be confirmed subject to a better understanding of the future financing lines. Every page has a footer stating: "© PRIVATE AND CONFIDENTIAL DOCUMENT. NOT FOR PUBLIC DISTRIBUTION".
Media blackout
Detailing the failure to report on the Integrity Initiative, 21st Century Wire asked “Was there a ‘D Notice’ issued by the British government forbidding mainstream media outlets from reporting on the embarrassing leak of this clandestine propaganda operation?” [6]
An example
| Page name | Description |
|---|---|
| Integrity Initiative/Cluster | Metastases from the IfS/II. Covert cells with a single leader, been used to exert clandestine influence from the London HQ, for example to promote particular opinions or to smear people it deems undesirable. |
Related Quotations
| Page | Quote | Author | Date |
|---|---|---|---|
| Integrity Initiative/Leak/7 | “Active Measures are currently and continuously in use by Russia across what they see as a single global theatre of operations. These Measures are designed to alter population perception to create an artificial reality that benefits Russia. This includes influence at many levels through existing societal frameworks and by undermining the rules of international governance... [Proposal of activities about purported Russian influence continues, to be staff by two experts and have a "proposed £100,00<a href="#cite_note-1">[1]</a> budget".] [The advice concludes:] This project is best undertaken outside direct government control to minimise the inevitable accusation of being part of an orchestrated state-sponsored active measure. Using the IfS extensive and trusted network, including its existing Integrity Initiative, can keep the project somewhat under the radar while still accessing state and non-state actors that may not be so open with central government approaches in this area.” | Unknown | 14 October 2018 |
| Integrity Initiative/Leak/7 | “* Ability to handle sensitive information, an awareness of acting on behalf of HMG and acting accordingly, and be party to strict non-disclosure agreement;” | Unknown | 14 October 2018 |
References
- ↑ a b Integrity Initiative/Leak/1 iihandbookv2.pdf
- ↑ a b c d e f Integrity Initiative/Leak iihandbookv2.pdf
- ↑ a b Integrity Initiative/Leak/1 iihandbookv2.pdf, 30 May 2018
- ↑ , 22 June 2018
- ↑ Integrity Initiative/Leak/2
- ↑ 21st Century Wire