Difference between revisions of "Exodus"
(Created page with "{{concept |wikipedia= |image=exodus_dropper.png |image_caption=One of the apps on the Google App Store which installed Exodus. |image_width=400px |start=2016 |end=2019 |consti...") |
|||
| Line 9: | Line 9: | ||
|interests= | |interests= | ||
}} | }} | ||
| − | '''Exodus''' is a piece of [[spyware]] for [[Android]] [[smartphones]], | + | '''Exodus''' is a piece of state-sponsored [[spyware]], developed by [[eSurv]]. Initially developed for [[Android]] [[smartphones]], it was installed by a variety of Italian language droppers on the [[Google Playstore]] from 2016-2019. It was later ported to [[iOS]].<ref>http://archive.fo/ZbC2p</ref> |
| + | |||
| + | Exodus was "equipped with extensive collection and interception capabilities" including reporting back data, screenshots and using microphone recordings. It was also able to hide itself and run even when the screen was apparently not running. It was named "exodus" after the address of one of its [[command and control server]]s - {{t|attiva.exodus.esurv.it}}. | ||
==Origins== | ==Origins== | ||
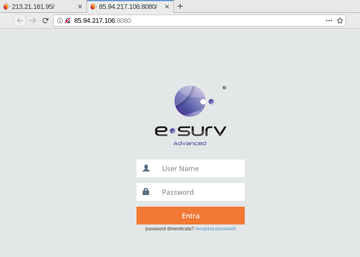
[[image:esurv_screen.png|left|360px|thumbnail|A control panel for an eSurv video surveillance system developed [[eSurv]].]] | [[image:esurv_screen.png|left|360px|thumbnail|A control panel for an eSurv video surveillance system developed [[eSurv]].]] | ||
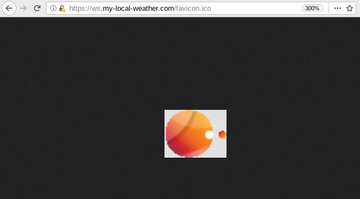
| − | [[image: | + | [[image:esurv_screen_command_and_control_server.png|left|360px|thumbnail|The Exodus command and control server, at {{t|ws.my-local-weather.com}}, which used an identical favicon to the above.]] |
A trail of evidence connects Exodus to [[eSurv]], an [[Italian]] company based in the southern city of Catanzaro. These included strings in the decompiled source, use of a TLS certificate used by eSurv's surveillance camera service, the TLS logo and [[internet]] addresses used by its command and control servers. | A trail of evidence connects Exodus to [[eSurv]], an [[Italian]] company based in the southern city of Catanzaro. These included strings in the decompiled source, use of a TLS certificate used by eSurv's surveillance camera service, the TLS logo and [[internet]] addresses used by its command and control servers. | ||
Revision as of 03:09, 30 July 2019
(spyware) | |
|---|---|
 One of the apps on the Google App Store which installed Exodus. | |
| Start | 2016 |
Exodus is a piece of state-sponsored spyware, developed by eSurv. Initially developed for Android smartphones, it was installed by a variety of Italian language droppers on the Google Playstore from 2016-2019. It was later ported to iOS.[1]
Exodus was "equipped with extensive collection and interception capabilities" including reporting back data, screenshots and using microphone recordings. It was also able to hide itself and run even when the screen was apparently not running. It was named "exodus" after the address of one of its command and control servers - attiva.exodus.esurv.it.
Contents
Origins
A trail of evidence connects Exodus to eSurv, an Italian company based in the southern city of Catanzaro. These included strings in the decompiled source, use of a TLS certificate used by eSurv's surveillance camera service, the TLS logo and internet addresses used by its command and control servers.
An eSurv developer whose LinkedIn resume suggested he had the required skill set to have worked on it, when queried, replied: "confidential information. I don’t think I can say anything about this ;)"[2]
Actions
"Exodus was programmed to act in two stages. In the first stage, the spyware installs itself and only checks the phone number and its IMEI — the device’s unique identifying number — presumably to check whether the phone was intended to be targeted. For that apparent purpose, the malware has a function called “CheckValidTarget” [reported as not functioning correctly] ... after running the check, the malware downloaded a ZIP file to install the actual malware, which hacks the phone and steals data from it."[2] Once installed, the main Exodus app could use hardware such as the microphone and the GPS to collect data, collect screenshots and had modules specifically designed to collect data from other apps including WhatsApp, Facebook, Gmail, Skype, Viber, IMO, Telegram, SBrowser, Calendar & Chrome.
Legal status
While "Using spyware with warrants or a judge’s authorization is, generally speaking, legal in most countries in Europe,"[2] Giuseppe Vaciago, an Italian lawyer who specializes in criminal law and surveillance, told Motherboard in 2019 that "I don’t think there are reasons to believe this spyware is legal." His reasoning included its ability to do "much more invasive activities than those prescribed by the law", the fact that the CheckValidTarget() routine did not function correctly & the fact that after installing the payload, the device was rendered less secure and more vulnerable to exfiltration of personal data by third parties -- in contravention of a ruling of the Italian Data Protection Authority which forbids the use of spyware which degrades phone security in this way.
Police shut down
On April 1, 2019, the Italian Police seized eSurv computers and shut down the Exodus infrastructure, on suspicion of illegal wiretapping.[3]
Distribution
The specific targets of Exodus, if any, remain unknown. The software, which was in the Play Store, reportedly infected the devices of hundreds of Italians.Google said it was below 1,000. The various different versions of Exodus were all hosted by the Google Play Store. Google, when alerted to the spying carried out by the app, removed reported that nearly 25 variants of Exodus were uploaded to the Google Play Store.
Exposure
The app was researched by Security Without Borders and highlighted by Motherboard in 2019,<rfe>https://motherboard.vice.com/en_us/article/43z93g/hackers-hid-android-malware-in-google-play-store-exodus-esurv</ref> a story which was picked up by various other outlets.[4]
References
- ↑ http://archive.fo/ZbC2p
- ↑ a b c Cite error: Invalid
<ref>tag; no text was provided for refs namedmo - ↑ https://www.vice.com/en_us/article/43z93g/hackers-hid-android-malware-in-google-play-store-exodus-esurv
- ↑ https://securityaffairs.co/wordpress/83102/breaking-news/exodus-malware-google-play.html